CDC-ON® Success Stories
Check out the companies below that have incorporated CDC-ON®/Services for their organizations and have realized massive cost savings.
Watchpoint Data
MSSP: Managed SOC Service Delivery: 40K EPS
~Yearly Saving: >$250K, since 2017.
Canauri
SaaS: Security Product Development
~Yearly Saving: >$300K, since 2018.
MSSP, USA
Managed SOC Service Delivery: 100K EPS
~Yearly Saving: >$400K, since 2020.
Insurance Client
Insurance: Managed EUC, VA-Patch Mgmt.
~Yearly Saving: >$450K, since 2021.
I-Exceed
Banking SaaS: Compliance, VA/PT.
~Yearly Saving: >$30K, since 2019.
St. Mary’s School
Edn: SOC, VA/PT, Health Check, IT
~Yearly Saving: >$60K, since 2022.
Robinson Cargo
Shipping and Logistics: CDC-ON® Managed SOC Subscription
~Yearly Saving: >$50K, since 2017.
Ennoventure
Technology Startup: CDC-ON® Managed SOC Subscription
~Yearly Saving: >$40K, since 2019.
Banking Finance Client
Cooperative Bank: CDC-ON® Managed SOC Subscription
~Yearly Saving: >$100K, since 2019.
Police Cyberdome
Govt. LEA: CDC-ON® Managed SOC Subscription
~Yearly Saving: >$100K, since 2016.
Muscat Electrical Distribution Company
Utility: SOC, VA/PT, Health Check, IT & OT
~Yearly Saving: >$600K, since 2020.
KIMS Hospital
Healthcare: SOC, VA/PT, Health Check, IT & OT
~Yearly Saving: >$600K, since 2022.
ECIL
Govt. Critical Sector: Managed SOC Service Delivery
Custom, Made-in-Ind SOC/SIEM Platform Development
~Yearly Saving: >$1M since 2021.
CDC-ON® Custom Use-Cases
CDC-ON®
Advanced Threat Hunting and SOAR
CDC-ON®
Uses Advanced Analytics to
Track Abnormal Network Activity
Outlier Detection
- Monitors remote outbound TCP connections
- Detects uncommon port usage
- Detects outliers using advanced algorithms
- Gathers remote destination details using automated response methods
Process and Actor Identification
- CDC-ON® uses relational analytics to identify and pin down process owners
- Identifies malicious programs by correlating file hash, process path, usage trend, etc.
- Identifies payload delivery by monitoring user activity
- Looks for similar attack patterns within n/w
Response Action
- Isolates infected machines
- Performs evidence collection on infected machines
- Enforces security measures to block any communication to/from attacker IP
CDC-ON®
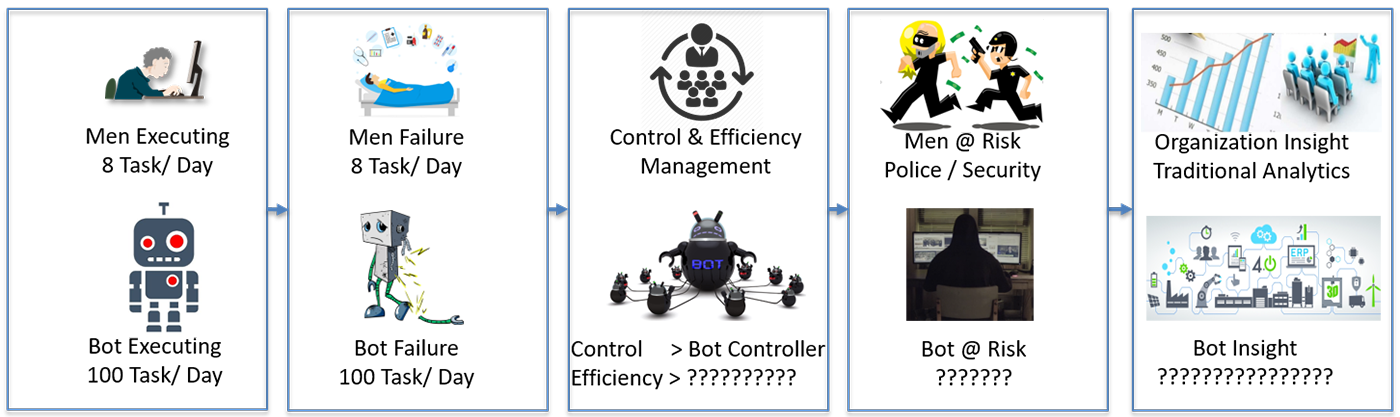
RPA BOT Farm Activity Monitoring
CDC-ON®
Bot Management & Analytics
Bot Efficiency
- Health and utilization
- ROI Statistics
- Availability statistics – Bot & dependencies
- Auto recovery using orchestration
- Automated ticketing & service management
- Support leading automation tools
- Bot capacity recommendations
Bot Security
- Bot farm vulnerability statistics
- Cyber attacks detection towards bots
- Unexpected network activities
- Unexpected user behavior
- Vulnerable payload transfers from/to bots
- Bot farm threat posture
- Bot security recommendations
Bot Insights
- Failure root cause identification
- Savings in comparison with health
- Effective utilization measures
- Projection of under utilized bots
- Bot farm executive dashboards
- Early warning on threats using TI
- Proactive failure detection and recovery
CDC-ON®
Design and Implement Security Analytics Platform
Our clients rely on CDC-On® and critical features like security, alerting, and machine learning. CDC-On® ingests, correlates, and analyzes vast quantities of information from thousands of systems across all of its member institutions in order to detect security breaches and cyber threats.
Client SOC security engineers then provide rapid, actionable intelligence back to its members so they can mitigate risks, close security gaps and prevent future attacks.
CDC-ON®
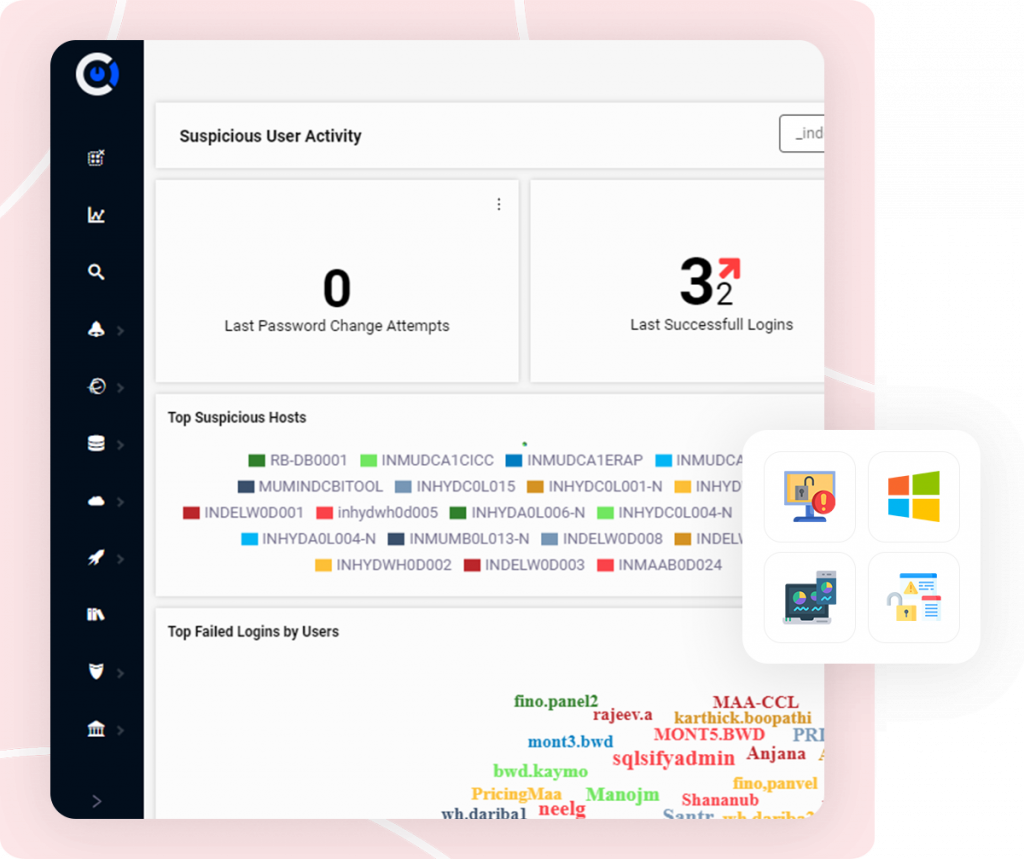
Security Analytics
Security Analytics
- Enhanced security monitoring coverage
- Reduce mean-time-to-detection
- Insight to organization security posture in real-time
- Advanced correlation and monitoring
- High speed log retrieval and historical data search
- Real-time alerting
SA Monitoring Process
- Advanced drill down dashboards
- Automate detection and remediation of threats
- Visual Analytics
- Automatic alerts
- Automated triaging/response actions
- Vulnerability detection
- KPI Monitoring, SOC+NOC
ROI
- Other SIEM/Analytics solution are high in cost
- Ease to enhance the infrastructure and upgrade
CDC-ON®
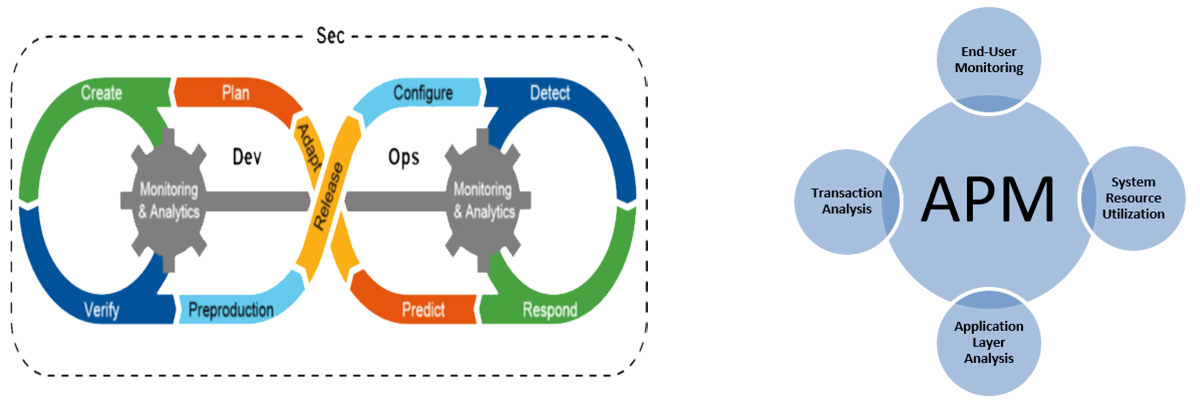
DevSecOps and APM
CDC-ON®
DevSecOps & APM Monitoring
Application Performance Insights
- Improve App performance
- Reduce mean-time-to-resolution
- App usage insight
- Comply with SLA
- End-User Experience
- Transaction Performance
- Trace Details
DevSecOps Monitoring
- CI/CD pipeline monitoring
- Automate detection and remediation of problems
- Visualize deployments
- Automatic alerting
- Automated testing visualization
- Vulnerability detection
- KPI Monitoring
ROI
- APM tools have been very expensive and targeted at only large enterprises. CDC-On® focus on SMB & Large Enterprises.
- The cost of downtime
- SLA Requirements
- Increasing Team Productivity
CDC-ON®
CDC-ON® in Action
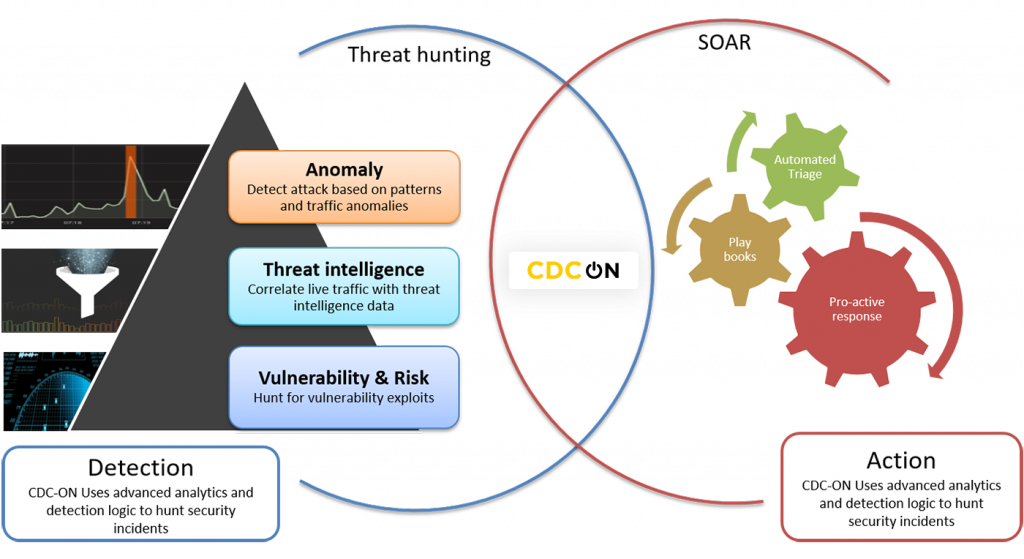
CDC ON®
Advanced Threat hunting and SOAR
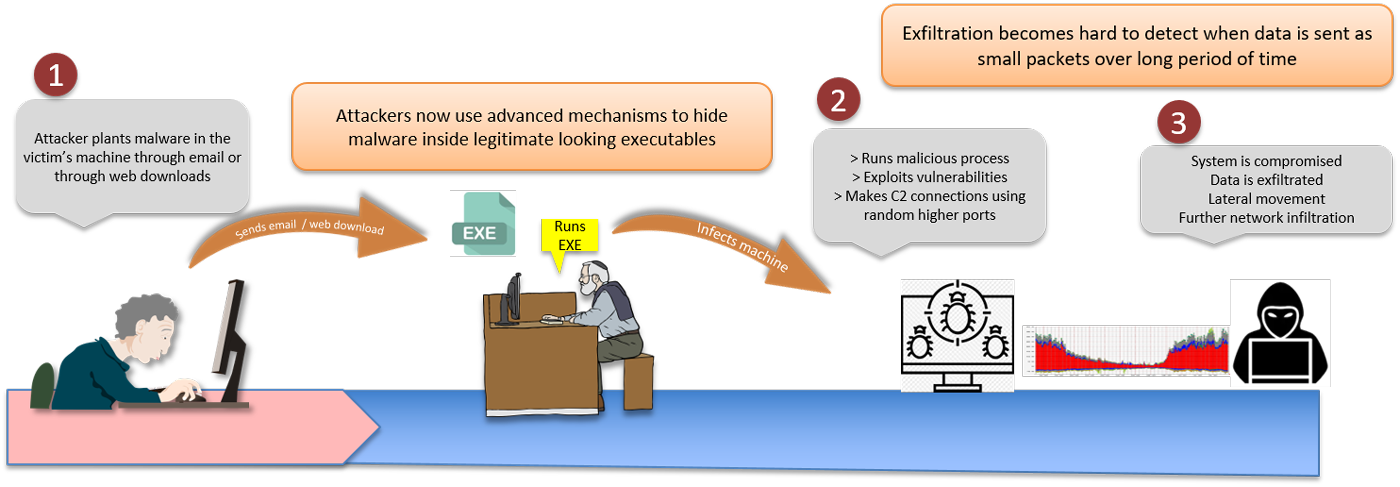
The threat landscape is ever changing in IT environments. Attacks and attack vectors are hard to detect with traditional detection rules and signatures. Cyber Security Analysts are expected to be armed with threat hunting skills to tackle such challenging situations.
CDC-ON® provides advanced analytics and workflows which makes threat hunting easy and effective. Attackers use infinite methods to infiltrate networks by exploiting vulnerabilities within network or people. Phishing emails, web ads, etc. are the most common methods employed by attackers. Latest security reports show high success rates for these attack mechanisms even today. Once getting into a host, the attacker hides himself and the malware within the victim’s machine. Hidden within usual traffic, the attacker exfiltrates data using different protocols and services. This makes traditional detection mechanisms ineffective against such attacks.
CDC-ON® uses advanced analytics to detect outliers from seemingly usual traffic. CDC-ON® can detect unusual traffic from baselined usual traffic and expected behaviors. Analysts can look into multiple dashboards that provide high visibility into user and network behaviors. Once unusual traffic is detected tracking down the true source process, host and user becomes the next step in threat hunting. This is where relational analytics of a SIEM tool can help an analyst without misdirecting him. CDC-ON® can provide instant visibility into process owner and related host activities. By correlating malicious traffic and process owner, an analyst can now look into malware delivery chains. Observing user activity and payload inspection during a specified time window will give insight into the method of delivery whether email or web traffic. Analysts can also look for similar patterns of traffic within the network to track down malware spread.
Once infection is confirmed, the next step is response action. CDC-ON® is integrated with SOAR platforms thus providing advanced responses like:
- Network isolation of host
- Evidence collection from infected host
- Enforce security measures by blocking malicious traffic at perimeter level
- Send ticket to an ITSM solution
This makes CDC-ON® unique from other SIEM tools in the market. CDC-ON® comprises of threat detection, analysis and response capabilities.

